In today’s digital world, where email is the backbone of business communication, cybercriminals are exploiting vulnerabilities with alarming sophistication. Business Email Compromise (BEC), a form of phishing attack, is one of the most financially damaging online crimes, costing businesses billions of dollars each year.
Understanding how BEC works and implementing protective measures is crucial for businesses of all sizes.
What is Business Email Compromise?
Business Email Compromise is a cyberattack where criminals impersonate a trusted party – such as a CEO, vendor, or business partner – to manipulate victims into transferring money, revealing sensitive information, or completing other fraudulent tasks. These scams rely heavily on social engineering and exploit human trust rather than technical vulnerabilities.
Common Types of BEC Attacks
- CEO Fraud: The attacker pretends to be a high-ranking executive and sends an email to an employee, typically in finance or HR, requesting a wire transfer or sensitive information.
- Vendor Impersonation: Cybercriminals pose as a vendor or supplier and send fake invoices or payment request to accounting departments.
- Account Takeover: Hackers gain access to legitimate business email accounts through phishing or credential theft, then use the account to send fraudulent emails.
- Payroll Diversion: Fraudsters trick HR or payroll departments into changing and employee’s direct deposit information to route payments into a criminal-controlled account.
- Gift Card Scams: Attackers impersonate executives, asking employees to purchase gift cards and send the codes for “urgent business needs”.
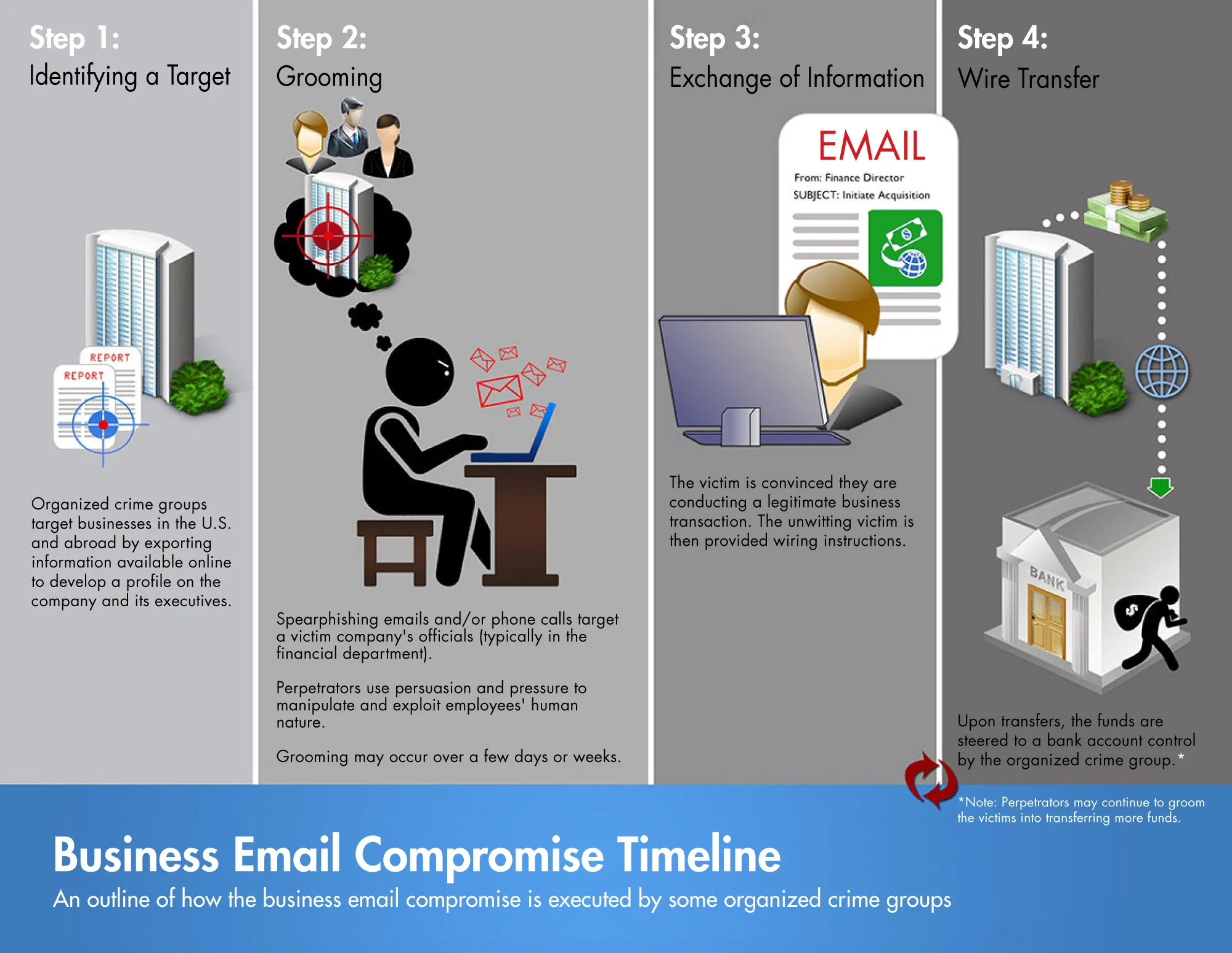
How Does BEC Happen?
BEC attacks rely on careful planning and execution. Here’s how cybercriminals typically operate:
- Reconnaissance: Attackers research their targets through LinkedIn, company websites, or social media to identify decision-makers and organizational structures.
- Spoofing or Hacking:
- Email Spoofing: Sending emails from a lookalike domain (e.g., @yourc0mpany.com instead of @yourcompany.com).
- Account Compromise: Using phishing emails or malware to gain control of legitimate email accounts.
- Social Engineering: Leveraging urgency, authority, or confidentiality to pressure employees into acting without verification.
- Execution: The attacker requests funds, data, or other valuable assets, often targeting busy employees during peak times to minimize scrutiny.
Why is BEC So Dangerous?
- Low Technical Barriers: Unlike other cyberattacks, BEC doesn’t require advanced hacking skills – just research, deceptions, and email spoofing tools.
- High Success Rate: These scams exploit trust and human error, bypassing traditional cybersecurity defenses like firewalls or antivirus software.
- Substantial Financial Losses: According to the FBI, BEC schemes caused over $2.7 billion in reported losses in 2022, and this number continues to rise.
How to Prevent Business Email Compromise
While no organization is entirely immune, implementing the following strategies can significantly reduce your risk:
- Strengthen Authentication:
- Use Multi-Factor Authentication (MFA) for email accounts to make it harder for attackers to gain access.
- Educate Employee:
- Conduct regular cybersecurity awareness training to teach employees how to identify phishing and social engineering tactics.
- Verify Requests:
- Always verify financial or sensitive requests through out-of-band communications, such as phone call or in-person confirmation.
- Implement Email Security Solutions:
- Use tools to detect email spoofing, phishing attempts, and suspicious activities.
- Monitor Email Activity:
- Regularly review account login activity for unusual behavior of logins from unfamiliar locations.
- Use Domain Protection:
- Configure Domain-based Message Authentication, Reporting, & Conformance (DMARC) to prevent spoofed emails from your domain.
What to Do if You’re a Victim of BEC
- Act Quickly:
- If funds have been transferred, contact your bank immediately to attempt a reversal.
- Report the Incident:
- Notify local law enforcement and file a complain with the FBI’s Internet Crime Complaint Center (IC3).
- Strengthen Security Post-Incident:
- Reset passwords, enable MFA, and review policies to prevent future attacks.
- Communicate Internally:
- Inform employees of the attack to ensure heightened vigilance and prevent further manipulation.
Conclusion
Business Email Compromise is a silent yet devastating cyberthreat. It thrives on trust and human error, making it essential for businesses to stay vigilant and proactive. By fostering a culture of security awareness and implementing robust safeguards, organizations can mitigate the risk of falling victim to these scams.
Protecting your business from BEC isn’t just about technology; it’s about empowering your team to recognize and respond to potential threats. Omni Threat Solutions is here to help with tailored training, assessments, and strategies to keep your business secure.
Would you like to explore how our services can fortify your business? Contact us today!