In the realm of security, the greatest vulnerability isn’t always technological—it’s human. Social engineering attacks exploit human psychology, manipulating individuals into divulging sensitive information or granting access to restricted areas. Despite sophisticated firewalls and security protocols, one well-crafted email or convincing phone call can bypass them all.
At Omni Threat Solutions, we specialize in identifying and mitigating these threats. This blog explores common social engineering tactics, real-world examples, and proactive steps to defend your business.
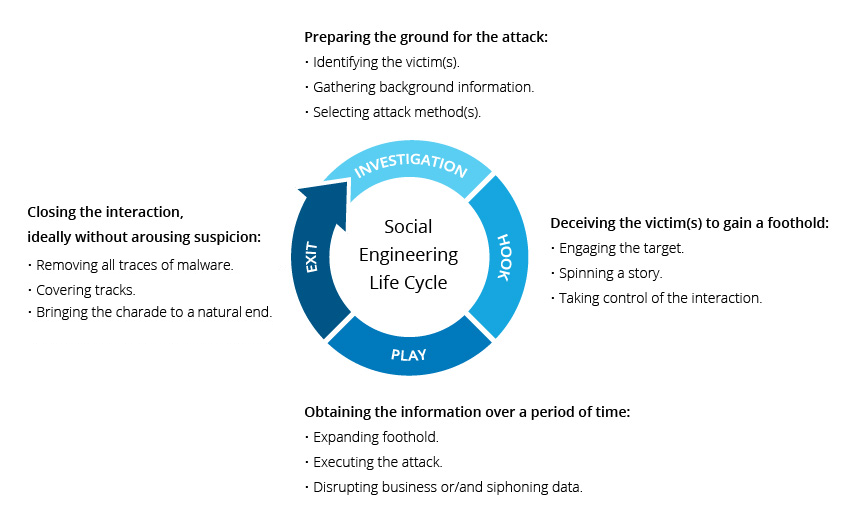
What is Social Engineering?
Social engineering is the art of manipulating people to gain access to confidential information or systems. Attackers often rely on trust, urgency, or fear to trick individuals into bypassing standard security measures.
Common targets include:
- Receptionists or front-line personnel.
- Employees who handle sensitive information.
- IT staff with privileged access.
Key Tactics Used in Social Engineering
- Phishing
- Attackers send deceptive emails that appear to be from trusted sources, urging recipients to click a malicious link or share sensitive information.
- Example: A fake email from “IT Support” requesting login credentials to fix an account issue.
- Attackers send deceptive emails that appear to be from trusted sources, urging recipients to click a malicious link or share sensitive information.
- Pretexting
- Here, the attacker invents a scenario to gain the target’s trust. This might involve impersonating a coworker, vendor, or government official.
- Example: Posing as an HR representative requesting employee data for “audit purposes.”
- Here, the attacker invents a scenario to gain the target’s trust. This might involve impersonating a coworker, vendor, or government official.
- Baiting
- Baiting lures victims with promises of rewards or tempting content, often in the form of USB drives left in public spaces or fake download links.
- Example: A USB labeled “Confidential: Payroll” left in an employee lounge.
- Baiting lures victims with promises of rewards or tempting content, often in the form of USB drives left in public spaces or fake download links.
- Tailgating
- This involves following an authorized individual into a secure area by exploiting politeness or trust.
- Example: Posing as a delivery driver and asking to be “buzzed in.”
- This involves following an authorized individual into a secure area by exploiting politeness or trust.
The Cost of Social Engineering Attacks
Social engineering attacks can lead to:
- Data breaches exposing customer or employee information.
- Financial losses due to fraudulent transactions.
- Reputational damage from publicized incidents.
One infamous example is the 2016 attack on a major tech company, where an attacker impersonated a CEO to obtain employee tax forms. The breach cost millions and eroded client trust.
Streamlining the design process.
- Simulated Social Engineering Tests
- We conduct controlled phishing campaigns, pretexting calls, and physical intrusion attempts to gauge your organization’s susceptibility.
- Employee Awareness Training
- Training empowers your team to recognize and respond to social engineering tactics. Our sessions include practical examples, role-playing scenarios, and tips for maintaining vigilance.
- Policy Review and Enhancement
- We assess your existing security policies, from email protocols to visitor management, and recommend updates to minimize risk.
Defend your Business Against the Human Element
Social engineering is a persistent and evolving threat, but with the right preparation, your organization can stay ahead. Omni Threat Solutions is here to help you build a culture of security that protects your assets and reputation.
Ready to strengthen your defenses against social engineering? Contact us to schedule an assessment or employee training session today.